Endpoint Detection & Response
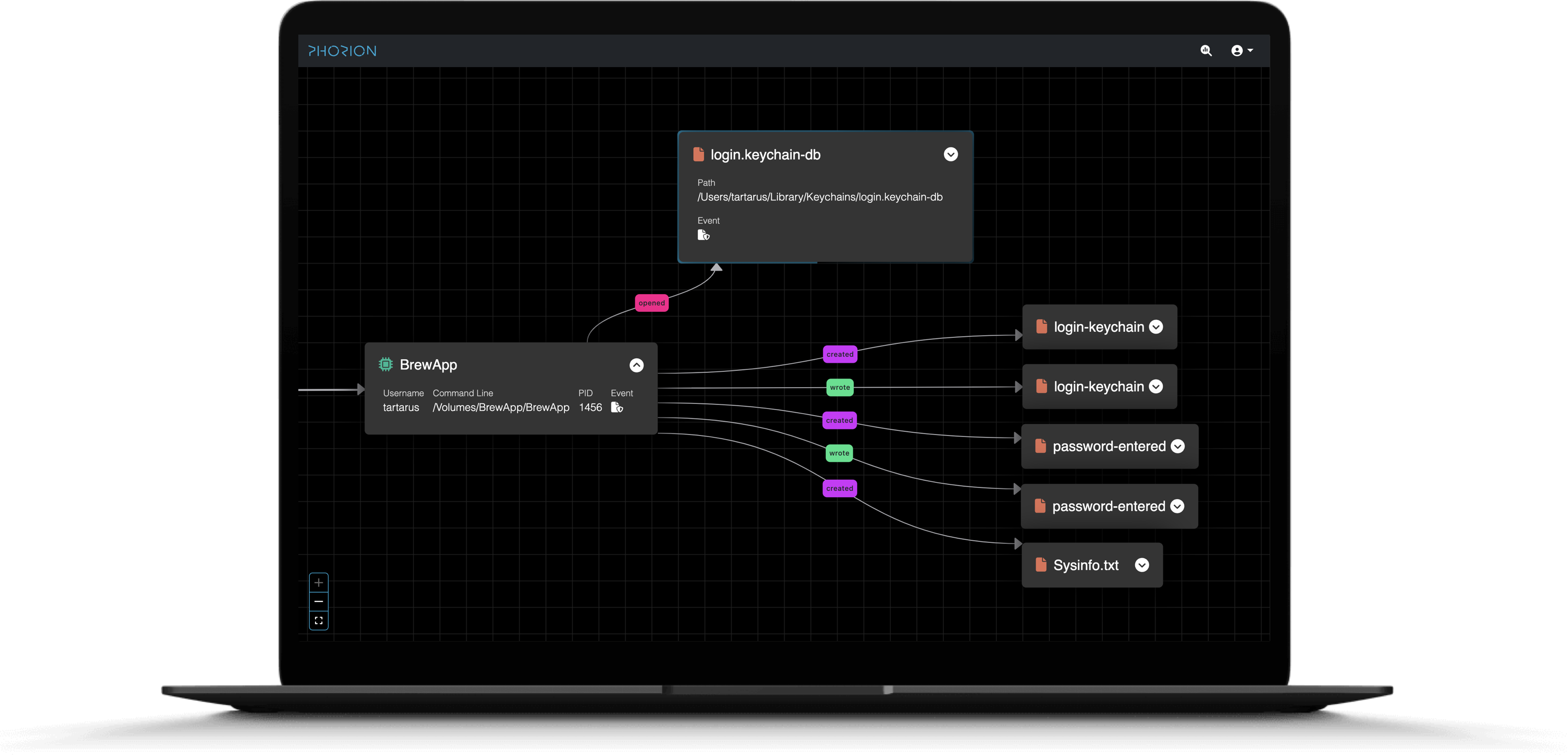
File Access Controls
Neutralize common macOS threats like infostealers by preventing unauthorized access to browser cookies and extension configurations. Phorion's file access control feature empowers security teams to restrict access to sensitive browser data to only necessary applications, significantly reducing your endpoints' attack surface.
DoubleYou Integrated
Phorion has partnered with Patrick Wardle and Mikhail Sosonkin’s DoubleYou to integrate advanced malware detection and prevention, perfectly complementing Phorion’s behavioral detection strategy for robust macOS security.

Performance Obsessed
Your users hate security products that slow down their devices? We do too. Phorion's agent is native code, built with performance in mind.
Features
Phorion was developed with an unwavering focus on macOS security. Each feature was crafted from years of experience of attacking and defending macOS estates.

Pre-built Detections
Phorion's out of the box detection capabilities are built upon the latest threat intelligence and years of experience attacking and defending macOS estates.
Detection development portal
Our customers are encouraged to bring their detection development expertise to the Phorion platform. Our custom rules permit Blue Teams to enhance the platform's capabilities with detections tailored to their own environments.
Rule tuning
Alerts can be tuned to your environment, ensuring that you are only alerted to the most critical threats. Phorion's detection development portal provides a simple and intuitive interface for tuning rules.
Process Termination
Automatically kill processes responsible for malicious activity. Phorion's process termination feature allows security teams to swiftly neutralize threats without analyst interaction for high fidelity detections.
Live Response
Access a live terminal to triage and remediate incidents in real-time. Phorion's live response tool is fortified with safeguards, ensuring you can address incidents confidently while preventing feature misuse.
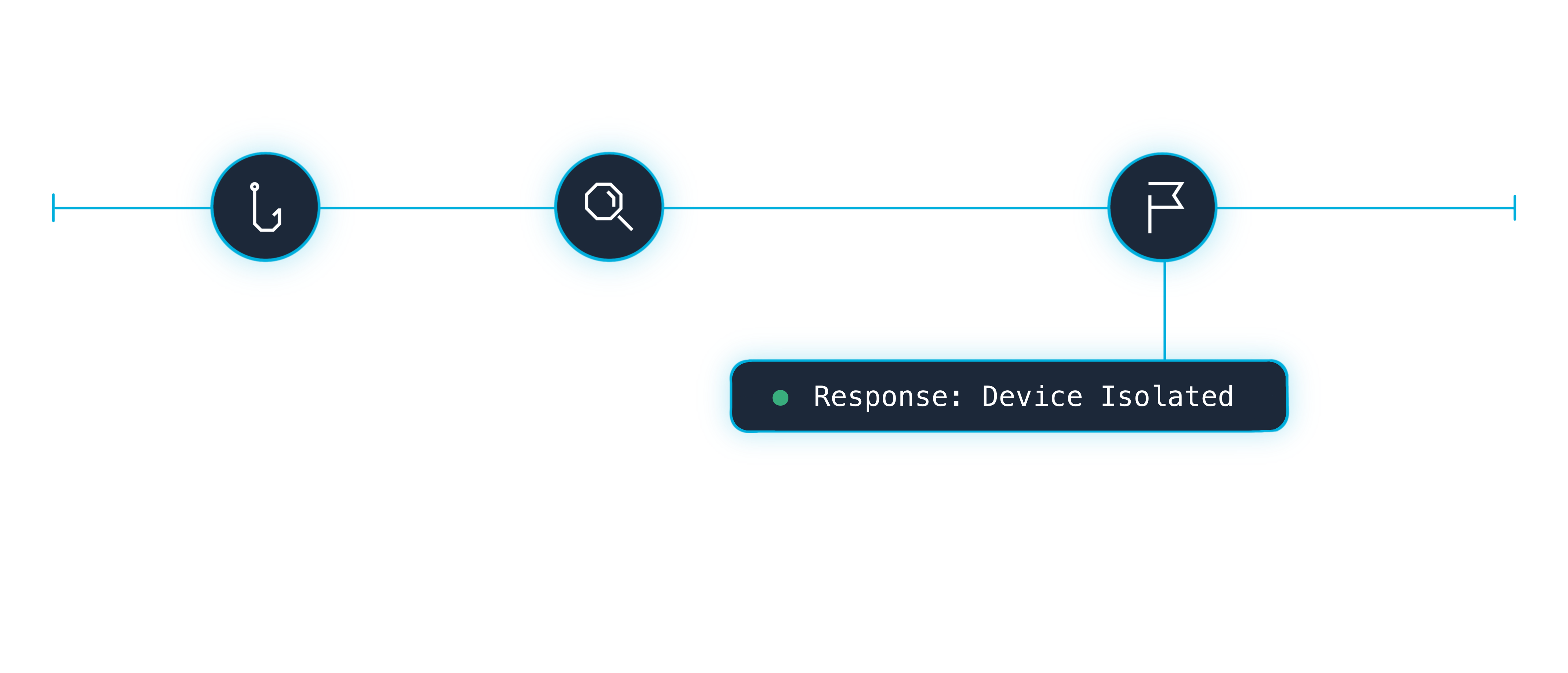
Device Isolation
Isolate compromised endpoints during incident response. With Phorion's network extension, analysts can block ongoing network connections from devices under investigation.
Endpoint Security Framework
The Phorion agent subscribes to Apple's Endpoint Security Framework for real-time event logging. Phorion continuously evolves the kind of ESF events being ingested, to evolve as Apple's framework matures.
File Read Events
A simple and yet critical feature of the Phorion agent - the ingestion of file read events. Implement a crown jewel defence by monitoring any and all access to your critically sensitive files.
Log Secret Scrubbing
Phorion’s customizable secret scrubbing feature removes sensitive information from log events before they leave your device. You can add your own secrets to ensure no critical data is exposed.
Network Telemetry
Leverage Phorion's network extension to monitor malicious connections, providing critical insight into the full kill chain for comprehensive threat detection.
Unified Log
Phorion's Unified Log module enables teams to utilise the abundance of information that gets stored within Apple's Unified log.
TCC Usage
Building upon Phorion's Kronos tool - utilise the Platform to evaluate TCC permissions and to track application usage. An invaluable insight for detecting suspicious application behaviour.
File Access Controls
Neutralize common macOS threats like infostealers by controlling access to sensitive files. Phorion's file access control feature empowers security teams to restrict sensitive file access to only necessary applications, significantly reducing your endpoints' attack surface.
Custom Hash Blocking
Proactively block known malicious files by leveraging custom hash blocking. Security teams can easily add hashes of known bad files to Phorion, ensuring these files are prevented from executing on endpoints.
Environmental Health Monitoring
Maintain a robust security posture by continuously monitoring the health of your macOS environment. Phorion's environment health monitoring feature provides real-time insights into endpoint configurations, ensuring compliance with security policies and identifying potential vulnerabilities before they can be exploited.
Continuous Threat Hunting
Phorion's macOS researchers continuously hunt for emerging threats, based on industry research, known TTPs and anomalous behaviour that stands out across our datasets. New detections are regularly added to the platform, ensuring your endpoints are protected against the latest threats.
Osquery Built-in
Empower your threat own threat hunts with Phorion's built-in osquery integration. Access a vast array of endpoint data through osquery's SQL-like queries, enabling your security team to perform custom investigations and uncover hidden threats within your macOS environment.
Persistence Monitoring
Identify and track the items that persist on each of your devices. Phorion's persistence tracking capabilities can be crucial during the investigation of a security incident.
Talk to our team
Phorion is the macOS-dedicated EDR built by researchers who've spent their careers breaking and defending Apple endpoints, using a paradigm shifting approach actually designed for the OS it protects.
Want to find out more? Get in touch and we'll set up a demo of the Phorion platform.


